 This article aims to explain what various DNS records are and how to use them. It is aimed at people hosting websites and email servers on a home server such as a raspberry pi.
This article aims to explain what various DNS records are and how to use them. It is aimed at people hosting websites and email servers on a home server such as a raspberry pi.
How DNS Works
DNS stands for Domain Name System. In a nutshell, it's the system that we use to translate human readable domain names (e.g. samhobbs.co.uk) into the Internet Protocol (IP) addresses for those services (e.g. 195.166.151.235). The DNS system has a strict hierarchy, and lookups are performed recursively using a client/server model. This means that when your computer asks for the IP address for "subdomain.example.com", the DNS resolver you are using starts at the top and works backwards to find the address. The servers at the top of the pyramid (root name servers) direct clients to the name servers reponsibe for Top Level Domains (TLD, e.g. .com), and that server in turn is able to tell the client which name server is authoritative for the second level domain (e.g. example.com), and so on. Usually for small sites, the DNS records for your domain are managed by your Domain Name Registrar. The DNS resolver doesn't have to perform all these lookups every time, because each record has a Time To Live (TTL) in seconds, which tells the client how long they can cache the information for until it should be refreshed. That's Time To Live (live free), not Live (live electrical circuit), which is how I first read it! There are loads of different types of DNS record, so I've picked the most important ones you might need or want to use. These are:
- DNS A - used to map a host name to an IP address
- Mail Exchanger (MX) - used to tell clients which hostnames are used for email services
- Sender Policy Framework (SPF) - used to define which servers are allowed to send email from your domain name
- Pointer (PTR) - the opposite of DNS A, this record maps an IP address to the hostname
For a website, you only need a DNS A record. For an email server, you need at least a DNS A record and an MX record; PTR and SPF records will help you get your email through spam filters. I'll be illustrating how to set up the different types of record using Namecheap, my Domain Name Registrar, as an example. If you haven't registered a domain name yet, I'd recommend Namecheap -avoid GoDaddy if you can, since they have some pretty horrible pricing practices and consistently back the wrong side when it comes to internet censorship acts like SOPA and PIPA.
 ModSecurity is a Web Application Firewall: a program that can be used to inspect information as it passes through your web server, intercepting malicious requests before they are processed by your web application. This tutorial will show you how to install ModSecurity on Apache, and configure it with some sensible rules provided by the Open Web Application Security Project's Core Rule Set (OWASP CRS), which will help to protect your server against SQL injection, denial of service attacks, malformed requests, cross site scripting attacks, and more. And yes, you can use this guide with your Raspberry Pi if you're running Raspbian, Ubuntu, or another Debian derivative on it.
ModSecurity is a Web Application Firewall: a program that can be used to inspect information as it passes through your web server, intercepting malicious requests before they are processed by your web application. This tutorial will show you how to install ModSecurity on Apache, and configure it with some sensible rules provided by the Open Web Application Security Project's Core Rule Set (OWASP CRS), which will help to protect your server against SQL injection, denial of service attacks, malformed requests, cross site scripting attacks, and more. And yes, you can use this guide with your Raspberry Pi if you're running Raspbian, Ubuntu, or another Debian derivative on it. 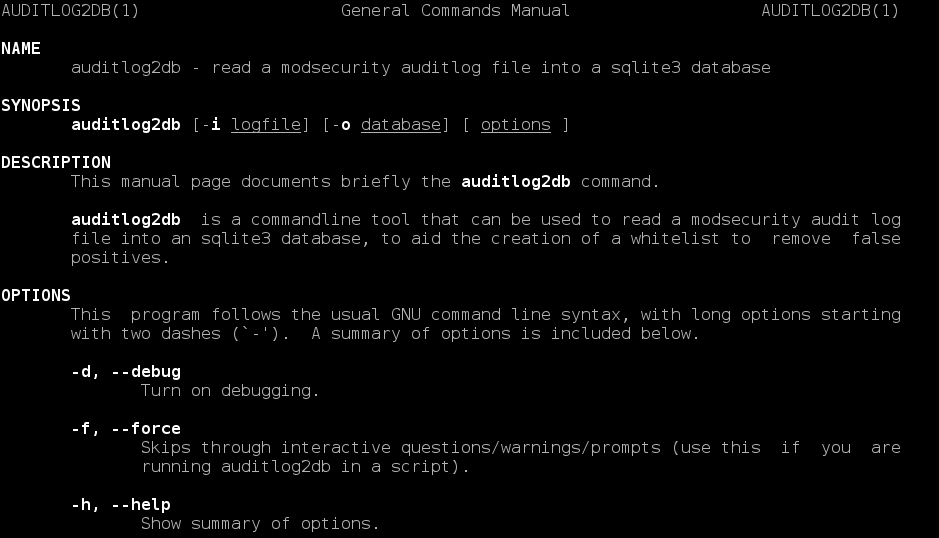 I have written a CLI utility for Ubuntu to import ModSecurity's audit log file into an sqlite database, which should be a great help to people building whitelists to reduce false positives. This supersedes my
I have written a CLI utility for Ubuntu to import ModSecurity's audit log file into an sqlite database, which should be a great help to people building whitelists to reduce false positives. This supersedes my  This article aims to explain what various DNS records are and how to use them. It is aimed at people hosting
This article aims to explain what various DNS records are and how to use them. It is aimed at people hosting 
 Google
Google 
