Apache ModSecurity Whitelist Generator Script
This script has been superseded by a commandline utility. Please visit this page for more information ModSecurity is a Web Application Firewall for Apache. It can monitor all of the traffic that is seen by your web server, including request headers and GET and POST data, and block dodgy requests. ModSecurity itself is actually just a rule engine; the clever part is in the rules you pass to it. Many people use the Open Web Appplication Security Project's (OWASP) Core Rule Set (CRS), an open source set of rules that ModSecurity can use to sift the wheat from the chaff, and foil some common types of attack. The CRS was written by studying known vulnerabilities and writing rules that would not only have prevented the attacks, but prevented other similar attacks too. Thus, ModSecurity provides a good all-round protection for your web server.

 If you run your own website, email server or other services like OwnCloud at home then you may find yourself in need of a SSL certificate. When you install Apache, it generates a self-signed "snakeoil" certificate that can be used to encrypt your session. However, while this certificate is useful for testing purposes, it falls short in a couple of important ways:
If you run your own website, email server or other services like OwnCloud at home then you may find yourself in need of a SSL certificate. When you install Apache, it generates a self-signed "snakeoil" certificate that can be used to encrypt your session. However, while this certificate is useful for testing purposes, it falls short in a couple of important ways: This tutorial will show you how to take a vanilla Raspbian image and turn it into a HTTP server hosting one or more WordPress website. I’ve previously written
This tutorial will show you how to take a vanilla Raspbian image and turn it into a HTTP server hosting one or more WordPress website. I’ve previously written 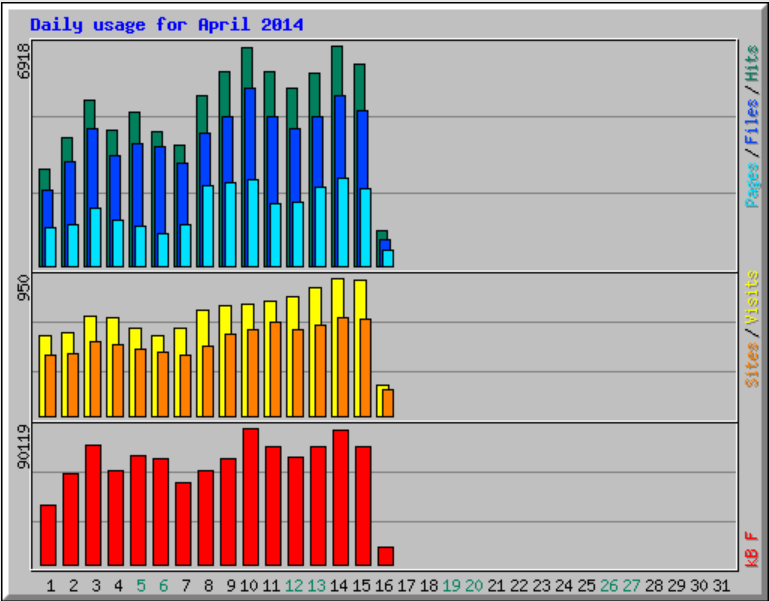 Google Analytics is everywhere. Seriously, everywhere. So much so that Google probably has a complete record of you hopping from site to site during your normal browsing, information that happens to be both extremely valuable to them and a pretty serious invasion of your privacy.
Google Analytics is everywhere. Seriously, everywhere. So much so that Google probably has a complete record of you hopping from site to site during your normal browsing, information that happens to be both extremely valuable to them and a pretty serious invasion of your privacy. 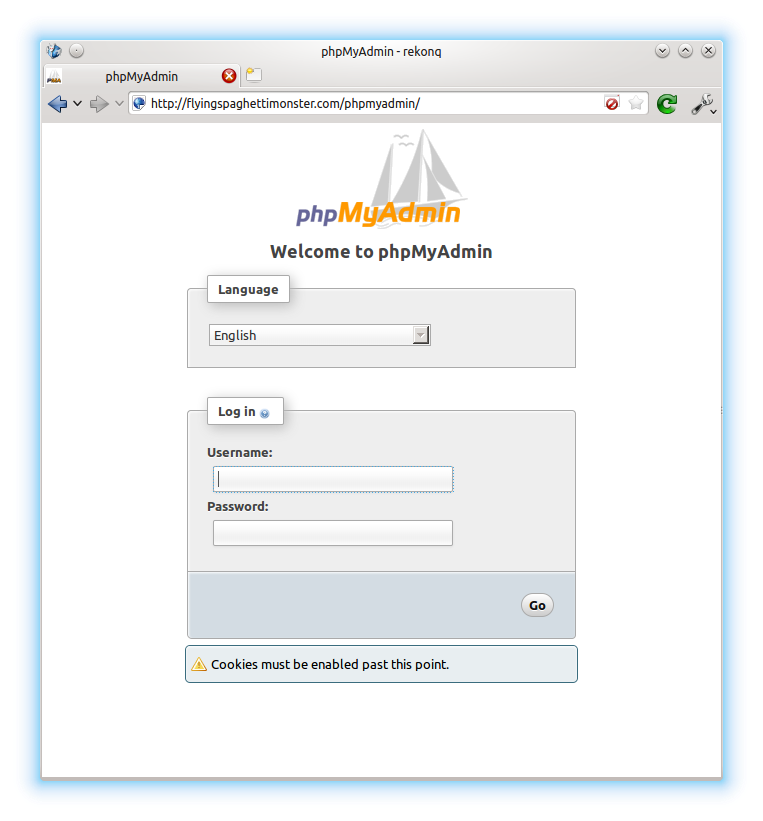 I recently installed a plugin for WordPress called “Better WP Security”. One of the features this plugin has is the ability to log all 404 errors, and temporarily or permanently block hosts that request too many non-existent pages in a short space of time. This is useful for blocking scripts that try to guess the location of your admin pages and then brute force their way in or exploit some specific vulnerability in the software. I noticed in the logs that one particular script (“w00tw00t.at.blackhats.romanian.anti-sec:)”) was checking my website to see if phpmyadmin had been installed but the setup script not run, requesting lots of pages like “phpMyAdmin/scripts/setup.php”. This got me thinking about securing the phpMyAdmin page a little, as I had pretty much just set it up and forgotten about it. I very rarely use it, but still wanted it installed just in case. So, the best solution was to simply disable access from outside my LAN.
I recently installed a plugin for WordPress called “Better WP Security”. One of the features this plugin has is the ability to log all 404 errors, and temporarily or permanently block hosts that request too many non-existent pages in a short space of time. This is useful for blocking scripts that try to guess the location of your admin pages and then brute force their way in or exploit some specific vulnerability in the software. I noticed in the logs that one particular script (“w00tw00t.at.blackhats.romanian.anti-sec:)”) was checking my website to see if phpmyadmin had been installed but the setup script not run, requesting lots of pages like “phpMyAdmin/scripts/setup.php”. This got me thinking about securing the phpMyAdmin page a little, as I had pretty much just set it up and forgotten about it. I very rarely use it, but still wanted it installed just in case. So, the best solution was to simply disable access from outside my LAN.